Your donation will support the student journalists of Marquette High School. Your contribution will allow us to purchase equipment and cover our annual website hosting costs. You may become a PATRON by making a donation at one of these levels: White/$30, Green/$50, Blue/$100. Patron names will be published in the print newsmagazine, on the website and once per quarter on our social media accounts.
In-Depth: Digital Threat to the Real World
Cybersecurity causes statewide issues and is a daily concern for students, staff
December 5, 2021
Students and staff continue to feel the effects of a district-wide data hack from Thursday, June 17, that has left many wary of how safe their information actually is online.
Alex Chen, junior, has worked heavily with coding for years and said he considers himself lucky for his experience working online has made him adept at avoiding security breaches with his own information.
“Cybersecurity is a growing concern in our world, and Rockwood is trying to keep up,” Chen said. “We need to both upgrade our systems and our training when dealing with cyber threats. Churches and schools are at risk due to their poor security posture and easy accessibility to hackers.”
Though there are many security risks that come with storing information online, Chen said there are easy steps that can be taken to ensure its safety. He said he is unhappy the breach has affected the learning environments within the school.
“In retrospect, it was only a matter of time,” Chen said. “I’m glad that they’re taking steps to fix it, but I still stand by what I originally said: security should be improved without effects on learning.”
Statewide Issues
RSD is not the only affiliation battling cybercriminals. Online threats pose a constant concern to various groups across the nation.
The Missouri government recently came under attack after a St. Louis Post-Dispatch reporter reported that the Missouri Educational Agency’s website contained a glitch displaying hundreds of thousands of social security numbers of those working in the educational system.
The reporter confirmed his findings with cybersecurity professionals before notifying the authorities of the problem; however, Missouri Governor Mike Parson called the reporter’s actions a crime, labeling it a “hack” of the teachers’ personal information.
“You can’t just be tampering around with someone’s website or trying to hack in,” said Aaron Branson, senior vice president of marketing for Netsurion. “So even if someone is trying with good intent or if they stumble on something accidentally, they should report it, not try and press the buttons to see if they can get in and prove a point.”
Netsurion is a company that provides managed cybersecurity services for small to medium sized businesses. Branson said the situation that occurred with the teachers’ social security numbers brings up the controversial topic of ethical hacking, which can be a profession as well.
Ethical hacking is the concept of businesses hiring hackers to test the strength of their cybersecurity systems. Branson said many larger companies have a cybersecurity team for ethical hacking, whereas smaller companies outsource the job to businesses such as Netsurion.
Though it can be done professionally, the controversy arises when done without the second party’s knowledge.

“Imagine you came home from vacation, pulled into the driveway and there’s a complete stranger in your house, and they said, ‘Hey great news. I was doing ethical break-ins and I found your house is vulnerable to break-ins as you can see, I am sitting in your house, eating your snacks and watching TV. Aren’t you glad I found out that your house is break-inable?’” Branson said.
Police Perspective
Chesterfield police Detective Timothy Turntine said anonymity has made cybercrimes more prevalent. Turntine began work in the past year with the Regional Computer Crimes Education and Enforcement Group (RCCEEG). There he works on a daily basis accessing confiscated devices and searching through the data recovered.
“Most of the crimes we are investigating, the suspects don’t even live in this country,” Turntine said. “We have so many crimes where people receive a phone call, and maybe they are foreign, and they own a shop in town, and the scammers take advantage of their not knowing the local laws so well, or people that just aren’t good with technology receiving emails they think are legitimate.”
A vast majority of cybercriminals seek out a financial scam in some way, and this is also commonly seen targeting younger generations through social media. Turntine said these criminals will often impersonate someone to achieve personal relationships.
Through this connection, criminals use blackmail to extort money as they threaten to release information or recordings that people are embarrassed of.
Financial extortion is not always the intent, however. Turntine said that often this impersonation can occur to obtain and potentially distribute pornographic images.
“That’s definitely something that students can fall victim to,” Turntine said. “There are definitely a great many terrible people out there that want those kind of images and want to share them.”
Turntine said as many of these crimes occur over long distances, his work consists less of solving the crime and more of recovering funds to prove the report being filed is legitimate.
“Be deliberate about everything you do online,” Turntine said. “Everything you do, feel like you know what you are doing.”
Malware attack
Deborah Ketring, RSD chief information officer, said she was notified that systems were working incorrectly on June 17 and ran tests that determined there was a malware attack. Ketring said the attack prompted RSD to revamp procedures and rebuild systems, she said.
On that date, Ketring said the malware was installed and machines were encrypted with ransomware, making it impossible to access files.
“Our first priority was to shut down our network and shut down systems to try and contain the damage,” Ketring said. “The plan was to contain it, isolate it and then begin our investigation to see what it was.”
After extensive examination from a forensic specialist, Ketring and her team were able to recover essential systems without paying the ransom.
The Active Directory Credentials, which are mainly used by staff and contain critical data, was the only resource that was negatively impacted, but the situation could have become more severe if the virus was caught later, Ketring said.
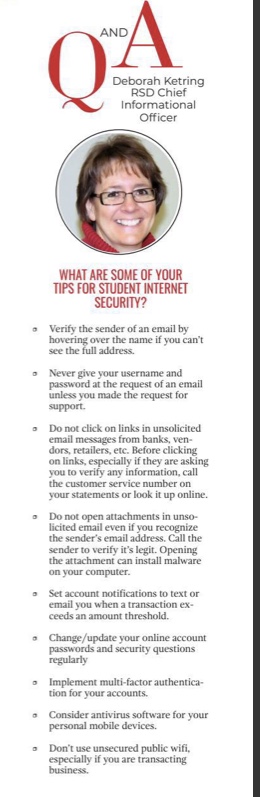
Ketring said students need to understand the risks of websites and links they visit.
“Sites and apps like Omegle may put students into positions where they are subjected to predatory actions without recourse,” Ketring said. “Remember, anything you post online, even if you delete it, may still be out there.”
To make the internet safer for students, Ketring said the technology department is in the process of revising and updating digital awareness, citizenship and cybersecurity resources for students.
Social Aspect
Password protection is not the only preventative measure students should take into consideration. Often the implications of forgotten items like computer webcams or smart devices don’t occur to people when trying to protect their security.
Additionally, a social media or online gaming presence opens up added risks if the proper precautions are not taken.
Lily McNulty, junior, is currently in an online relationship over Discord, an instant messaging and digital communication platform. McNulty said the experience of dating online is not any different from dating in-person – instead of meeting, her and her significant other text or call each other.
“It’s not that much different,” McNulty said. “I mean I feel like It’s been a pretty solid dating experience.”
McNulty said she has faced risks in e-dating since the person on the other side of the screen is unknown. She said after talking to users for an extended period of time, it is easier to tell if someone is genuine or not.
“It comes with experience like I’ve been online for so long that I kinda know what’s happening at this point,” McNulty said.
In addition to e-dating, McNulty has also visited Omegle, a platform where users can socialize without registering. She said she does not recommend visiting the site due to the age requirement and the people who frequent the site.
Tavian Kerber, junior, said he is an avid video game user and spends up to 30 minutes a day playing games like Clash Royale and games on his PlayStation Four. Kerber said he enjoys hanging with friends both in-person and online.
“I like hanging out with my friends more in-person, but it is fun online because we still get to talk,” Kerber said.
The biggest risk of playing online games, Kerber said, is not knowing who is on the other side of the screen, especially when connecting with anonymous gamers.
“I mean most of the games are pretty protected through the company, but it is a little weird,” Kerber said.
Aiden Emert, senior, said cybersecurity attacks can happen anytime someone jumps online, even if they are at home. Emert said attacks are most common through online, player versus player video games.
Emert is the In Game Leader (IGL) for MHS’ Valorant eSports team. Valorant is a player versus player, first-person shooter that requires players with great individual skill but a team to work together and win. In most cases, players have to play with and against strangers, some with malicious intents.
Emert said the most malicious players often go for another’s IP address, or the number that is associated with a person’s internet, by sending large amounts of information that eventually overloads and destroys a person’s connection.
Emert said if someone does happen to fall victim to an attack, the best thing to do is to unplug the router and wait several minutes or hours to rest the connection.


